Introduction
For end users to have a good experience interacting with any IT systems these days, Single Sign-On (SSO) is a must-have. I can’t emphasize enough how annoying and non-productive it is to log in multiple times to access corporate resources or systems. When using Azure Virtual Desktop (AVD) or Windows 365, there is no exception configuring SSO is a must.
SSO for Entra hybrid joined AVD hosts and Cloud PCs
Configuring SSO for Entra joined devices is straightforward for AVD and Windows 365. Entra hybrid joined devices have some more requirements that need to be in place such as Kerberos server object in Active Directory and Microsoft Entra authentication for RDP. As an optional setting, we can hide the consent prompt dialog this is however highly recommended if you ask me.
To boost the deployment of SSO for Entra hybrid joined AVD and Windows 365 devices, I’m using a script I created to optimize configuration time and avoid mistakes when setting up Microsoft Entra authentication for RDP and hide the consent prompt dialog. To be fair, my script isn’t revolutionary compared to what you can find in Microsoft’s documentation deployment steps. I have, however, combined a few steps, such as including the creation and specification of the required dynamic group and the installation of Microsoft Graph modules.
Running the script
First, edit the parameters $EntraIDGroup and $DynamicDeviceRule to whatever fits your environment and needs.
$EntraIDGroup: This is what the dynamic group name will be in Entra ID. If you specify a group that already exists it will use that throughout the deployment.
$DynamicDeviceRule: Specify the dynamic device rule that will “catch” either AVD hosts and/or Cloud PCs.
As an example, I will call my dynamic group All AVD Hybrid Devices with the following rule device.displayName -startsWith “avd-“.

When running the script it will first install and import the required modules and you will then receive an authentication prompt to login to Microsoft Graph.
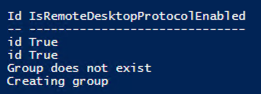
It will then set the RemoteDesktopProtocolEnabled to True for Windows Cloud Login and Microsoft Remote Desktop. When that is completed it will check if the group name that is provided already exists if not it will create a new group in Entra ID.
In the end, it will map the dynamic group to the Remote Desktop Security Configuration.

Closing words
I hope this script gives you a small boost with the configuration of SSO for Entra hybrid joined AVD hosts or Cloud PCs, especially if you are a consultant and regularly are helping organizations with setting up AVD and Windows 365 environments.
