I have come over many errors when creating Android and Android Enterprise/for work Wifi profile to authenticate with certificate.
there seems to be a bug in the normal wifi profile creator in Microsoft Intune. The only way I have succeeded to create Wifi profile for Android to validate with a certificate was with custom OMA-URI string.
To do before deploying Wifi profile:
1. Deploy RootCA to device
2. Deploy intermediate certificate ( if you have one)
3. Deploy user Certificate to device
To configure Custom Wifi profile do the following:
Go to Azure portal and navigate to Intune from “All Services” on top.
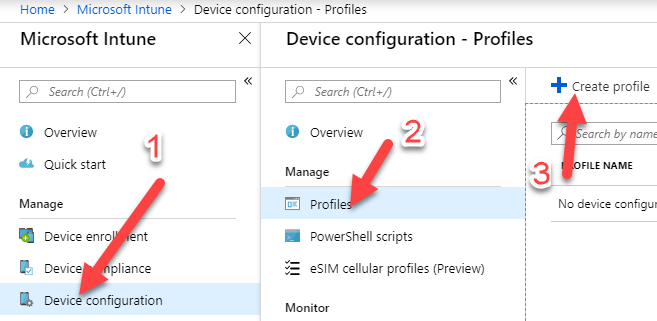
Create a profile with the following values:
Name: Type the name of your profile
Platform: Choose “Android” or “Android Enterprise” it will work for both
Profile Type: Custom
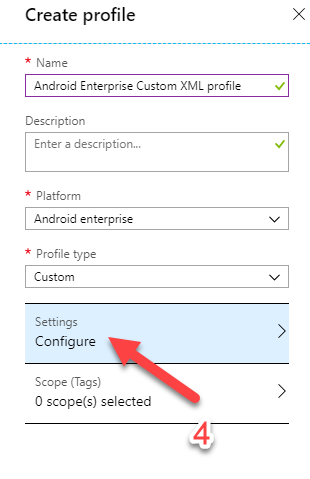
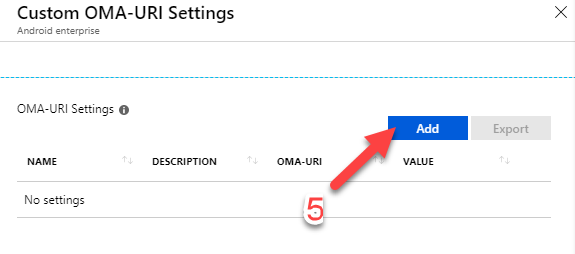
Configure OMA-URI Settings with the following value:
Name: Corporate WiFi
OMA-URI: ./Vendor/MSFT/WiFi/Profile/SSIDNAME/Settings
Data Type: String
Value: See XML below
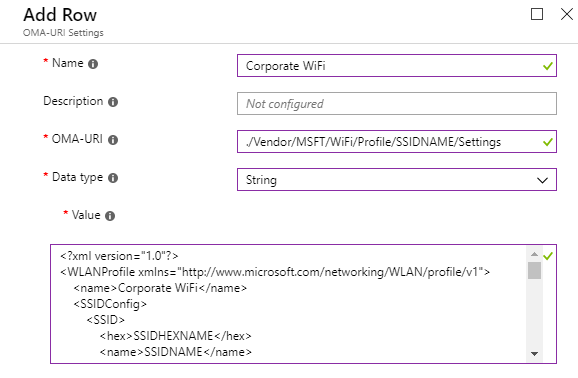 YOU HAVE TO REPLACE THE FOLLOWING VALUES WITH YOUR OWN:
YOU HAVE TO REPLACE THE FOLLOWING VALUES WITH YOUR OWN:
1. SSIDNAME: Replace “SSIDNAME” with your broadcast SSID in the OMA-URI setting above and in XML text ( Line7 ).
2. SSIDHEXNAME: Replace “SSIDHEXNAME” with your broadcast SSID hex name in the XML text(Line6). ( use text to hex converter to find your SSID hex value)
3. TrustedRootCA: Replace the “aa” in the XML text(Line45), with you RootCA thumbprint that you have deployed to your devices.
4. IssuerHash: Replace the “bb” in the XML text(Line53), with you intermediate thumbprint that you have deployed to your devices.
NOTE!: if you don’t use Intermediate Certificate replace “bb” with your RootCA Thumbprint
<?xml version="1.0"?>
<WLANProfile xmlns="http://www.microsoft.com/networking/WLAN/profile/v1">
<name>Corporate WiFi</name>
<SSIDConfig>
<SSID>
<hex>SSIDHEXNAME</hex>
<name>SSIDNAME</name>
</SSID>
</SSIDConfig>
<connectionType>ESS</connectionType>
<connectionMode>auto</connectionMode>
<MSM>
<security>
<authEncryption>
<authentication>WPA2</authentication>
<encryption>AES</encryption>
<useOneX>true</useOneX>
<FIPSMode xmlns="http://www.microsoft.com/networking/WLAN/profile/v2">false</FIPSMode>
</authEncryption>
<PMKCacheMode>disabled</PMKCacheMode>
<preAuthMode>disabled</preAuthMode>
<OneX xmlns="http://www.microsoft.com/networking/OneX/v1">
<cacheUserData>false</cacheUserData>
<authMode>User</authMode>
<EAPConfig>
<EapHostConfig xmlns="http://www.microsoft.com/provisioning/EapHostConfig">
<EapMethod>
<Type xmlns="http://www.microsoft.com/provisioning/EapCommon">13</Type>
<VendorId xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorId>
<VendorType xmlns="http://www.microsoft.com/provisioning/EapCommon">0</VendorType>
<AuthorId xmlns="http://www.microsoft.com/provisioning/EapCommon">0</AuthorId>
</EapMethod>
<Config xmlns="http://www.microsoft.com/provisioning/EapHostConfig">
<Eap xmlns="http://www.microsoft.com/provisioning/BaseEapConnectionPropertiesV1">
<Type>13</Type>
<EapType xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV1">
<CredentialsSource>
<CertificateStore>
<SimpleCertSelection>true</SimpleCertSelection>
</CertificateStore>
</CredentialsSource>
<ServerValidation>
<DisableUserPromptForServerValidation>false</DisableUserPromptForServerValidation>
<ServerNames></ServerNames>
<TrustedRootCA>aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa </TrustedRootCA>
</ServerValidation>
<DifferentUsername>false</DifferentUsername>
<PerformServerValidation xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">false</PerformServerValidation>
<AcceptServerName xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">false</AcceptServerName>
<TLSExtensions xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV2">
<FilteringInfo xmlns="http://www.microsoft.com/provisioning/EapTlsConnectionPropertiesV3">
<CAHashList Enabled="true">
<IssuerHash>bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb </IssuerHash>
</CAHashList>
<EKUMapping>
<EKUMap>
<EKUName>Encrypting File System</EKUName>
<EKUOID>1.3.6.1.4.1.311.10.3.4</EKUOID>
</EKUMap>
<EKUMap>
<EKUName>Secure Email</EKUName>
<EKUOID>1.3.6.1.5.5.7.3.4</EKUOID>
</EKUMap>
</EKUMapping>
<ClientAuthEKUList Enabled="true">
<EKUMapInList>
<EKUName>Encrypting File System</EKUName>
</EKUMapInList>
<EKUMapInList>
<EKUName>Secure Email</EKUName>
</EKUMapInList>
</ClientAuthEKUList>
</FilteringInfo>
</TLSExtensions>
</EapType>
</Eap>
</Config>
</EapHostConfig>
</EAPConfig>
</OneX>
</security>
</MSM>
</WLANProfile>

HI
Does this only apply to work profiles? I have deployed an Android WiFi profile to our corporate owned, fully managed devices for certificate authentication and while the policy applies the connection does not get configured on the device.
Many thanks
Hi.
Yes this only apply to work profile
Hello,
I have use case to provide SSID +Username+ password within Custom XML of android devices
I followed below doc for creating Custom xml but where should i keep username
https://docs.microsoft.com/en-us/mem/intune/configuration/wi-fi-profile-shared-key
Above doc only says preshared key but no mention about username
The XML i’m using dosent have username and password, it only has password requirement.
i haven’t configured your scenario
sorry.
The XML i’m using dosent have username and password, it only has password requirement.
i haven’t configured your scenario
sorry.
Do i have to give space between aa aa aa (thumbprint)?
Yes i have space between aa aa aa
Hi Morten,
If we deploy a wifi profile like this, and the user somehow deletes the wifi off his device, will the profile be deployed again to the device?
If not, can you think of a way to trigger the profile to be deployed again?
Thanks!
Morten,
What if we have more than one Trusted RootCA, can I add a second line in Server Validation
aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa aa
bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb bb
Hello All,
do you have an idea how to configure the XML file for an EAP-TLS configuration ?
Thank you very much