Azure provides a simple way to connect on-premise workstations to Azure resources like VM and other services with a Point-To-Site VPN. This can be really handy if you have some external partners that need to connect to your environment in Azure, or just have a couple of users that needs special access to some services in Azure.
To set it up I will create an Azure VPN Gateway, and spin up a VM and try to connect from an on-premise Hyper-v machine.
I will only use the Azure portal to configure the Azure environment but on my Github, I have uploaded how to created Azure VNET and VPN Gateway with Powershell. There are also how to create a self-signed certificate in that script.
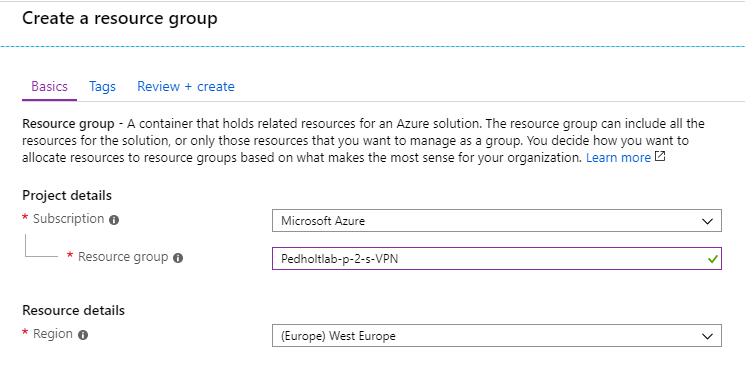
- Create a new resource group. that will hold our ressources for both VM, VNET and VPN Gateway.
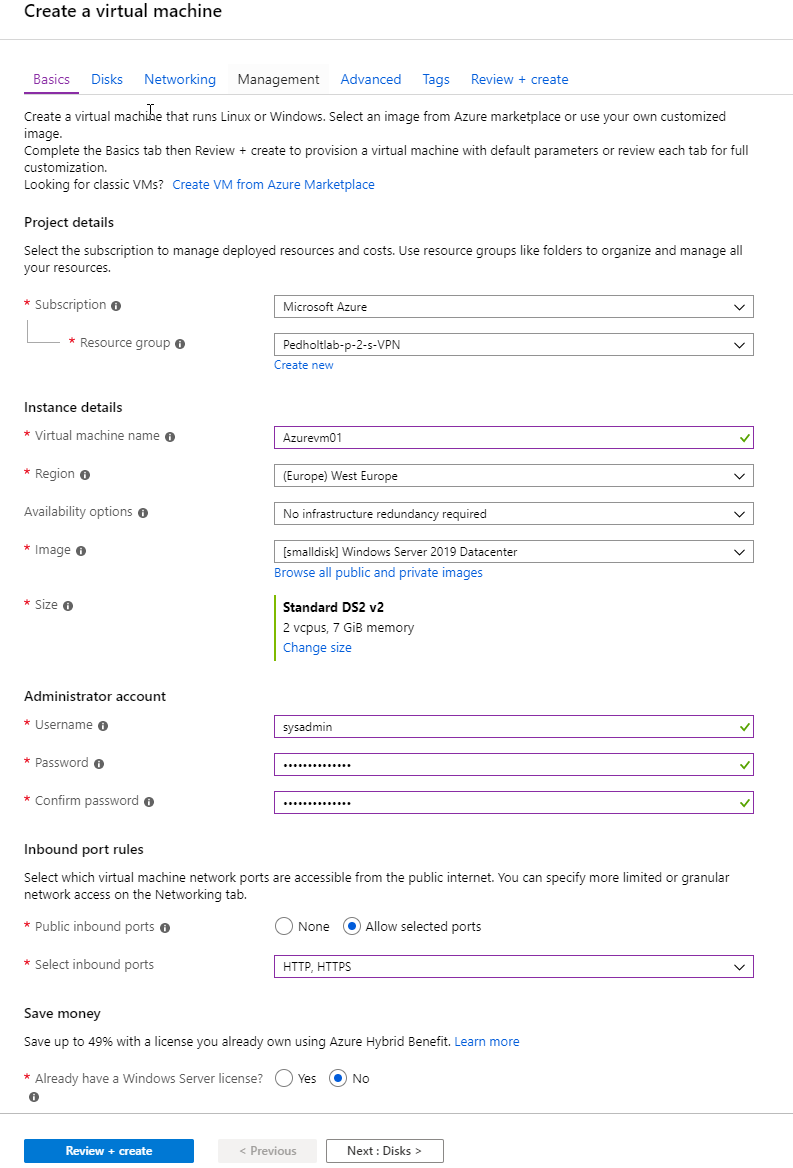
2. Create a virtual machine indside our new resourcegroup
Select Disk type for the VM.
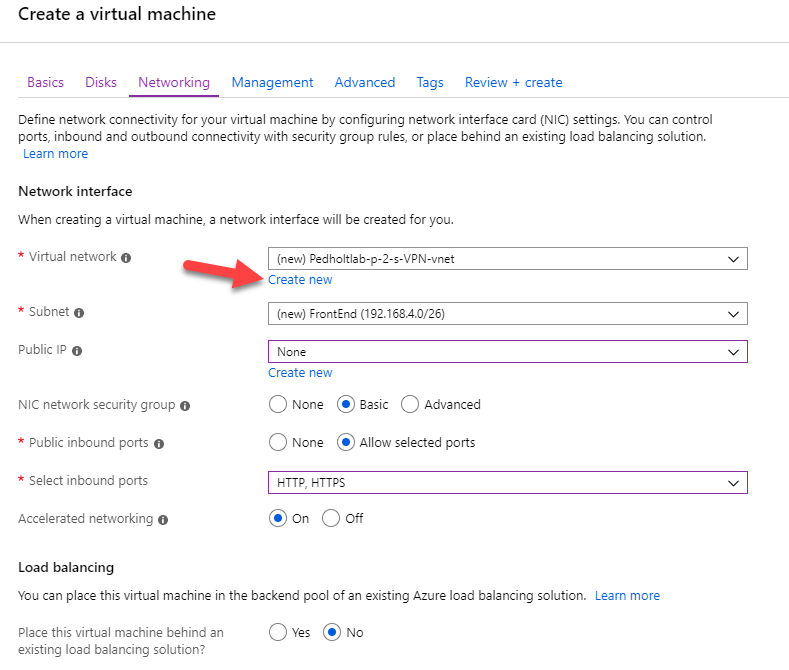
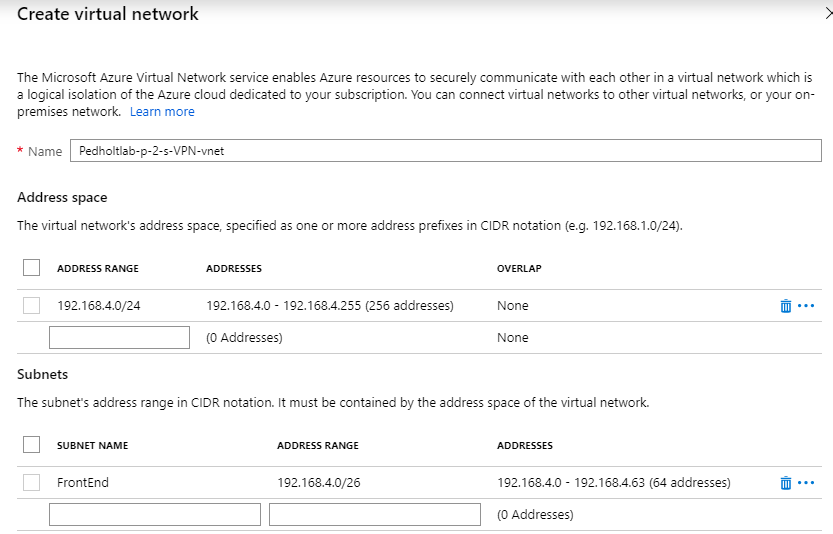
Create a virtuel network for both the VM and VPN to be in.
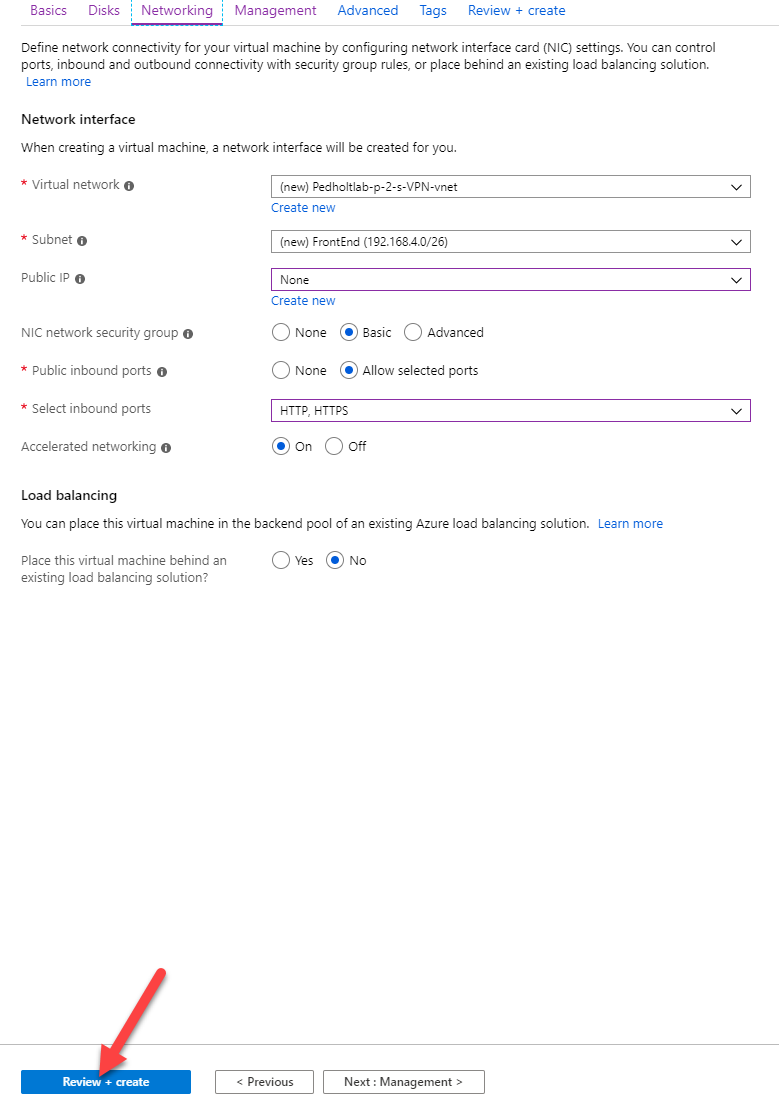
i will not have a PublicIP for my VM, i define address and subnet range of the VNET.
Now create the VM.
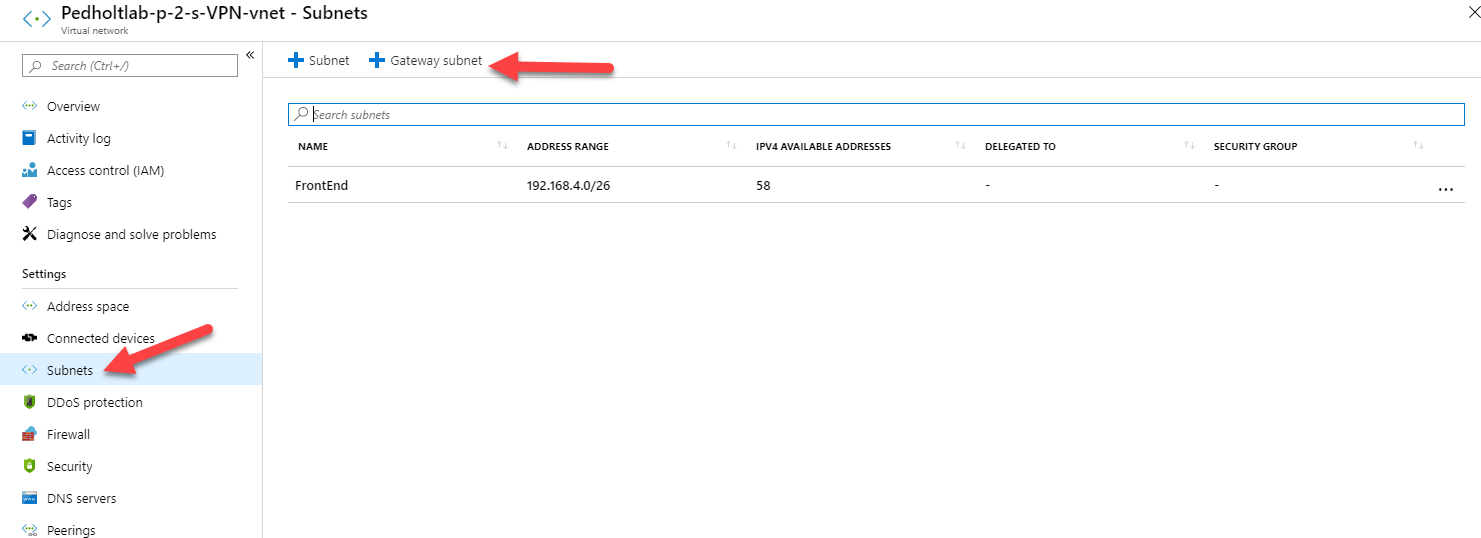
3. When the deployment of our virtuel network is done, find it and go to subnet settings, and create a new gateway subnet.
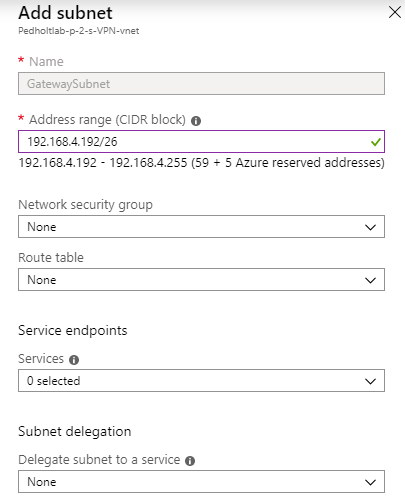
Define the gateway subnet range, this is the subnet the our VPN gateway will use.
4. Now we have our VNET comepleted, we can create a Virtuel Network Gateway, that will hold the configuration for our Point-To-Site VPN.
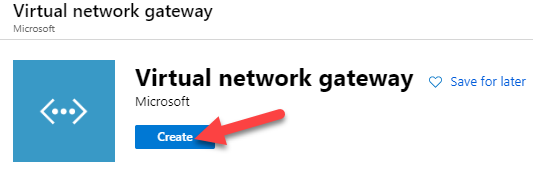
Fill out the configuration for the new virtual network gateway, and create it. it might take out to 1 hour, before the gateway are ready.
Go out and take a cup of coffee, or contiune to the step 5.
To choose the right SKU look at the documentations from Microsoft
https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-about-vpngateways
5. Create a self signed certificate, first we create a Root certificate and then a Child certificate. When child certificate is created export it as .pfx with private key.
NOTE: Before the clients can connect to the VPN, they need to install the Child certificate and not the Root. The Root will only be used on the VPN configuration.
To create a new Root Certificate run the following powershell command.
$filepathforcert = "C:\cert\P2SRootCert"
$P2SRootCertName = "P2SRootCert.cer"
$cert = New-SelfSignedCertificate -Type Custom -KeySpec Signature -Subject "CN=P2SRootCert" `
-KeyExportPolicy Exportable -HashAlgorithm sha256 -KeyLength 2048 -CertStoreLocation `
"Cert:\CurrentUser\My" -KeyUsageProperty Sign -KeyUsage CertSign
You will now see that you have a P2SRootCert under your personal Certificate store.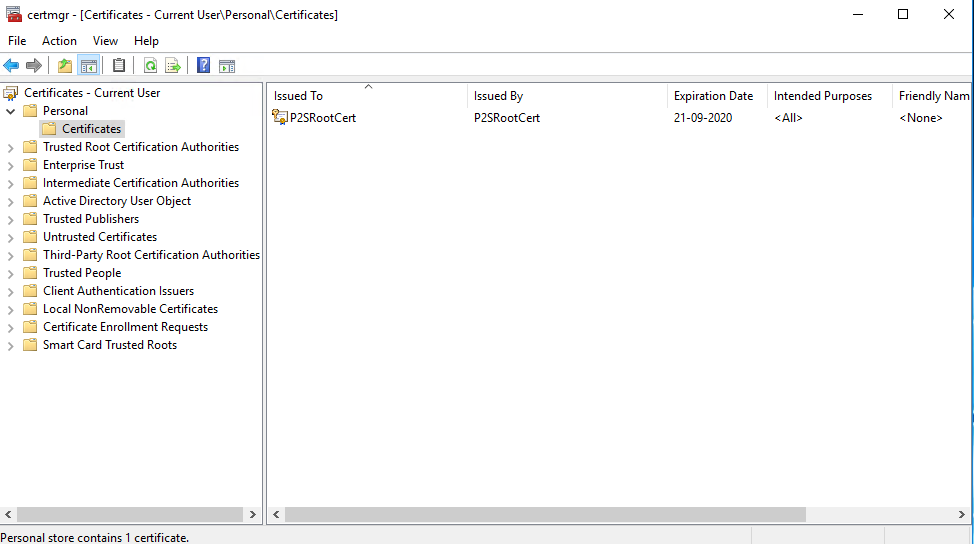
Now we need to create our Child certificate. In Powershell run the following commands.
Get-ChildItem -Path “Cert:\CurrentUser\My”
The output should be the thumbprint of our new P2SRootCert.
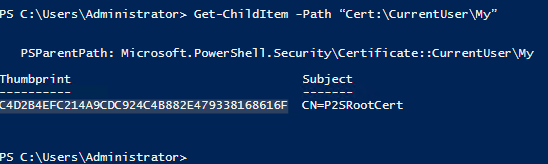
Copy the thumbprint and paste it in after “Cert:\CurrentUser\My\Thumbprint” in the next command.
$cert = Get-ChildItem -Path "Cert:\CurrentUser\My\C4D2B4EFC214A9CDC924C4B882E479338168616F"
New-SelfSignedCertificate -Type Custom -KeySpec Signature ` -Subject "CN=P2SChildCert" -KeyExportPolicy Exportable ` -HashAlgorithm sha256 -KeyLength 2048 ` -CertStoreLocation "Cert:\CurrentUser\My" ` -Signer $cert -TextExtension @("2.5.29.37={text}1.3.6.1.5.5.7.3.2")
Now we should have a new P2SChildCert in our personal certificate store.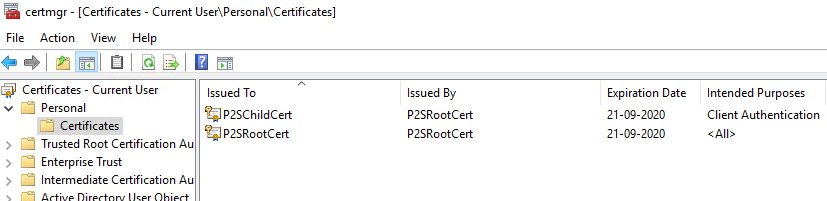
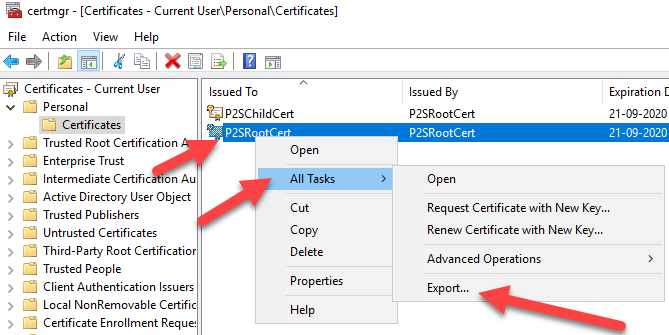
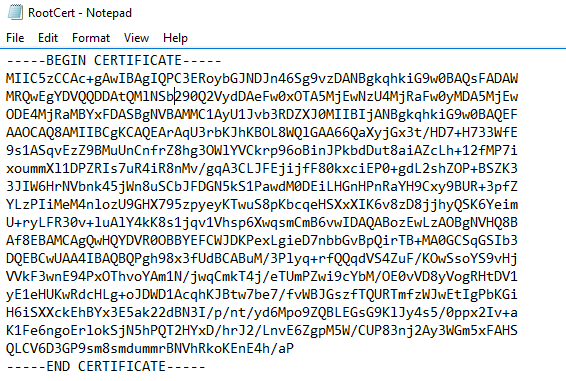
Now we need to get the export our P2SRootCert certificate data to import it into our Azure VPN Gateway.
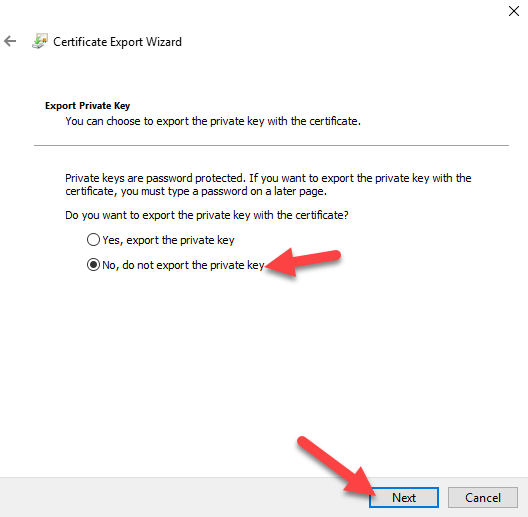
Find your Rootcertificate, and export it to Base-64 Encoded x.509 without a private key.
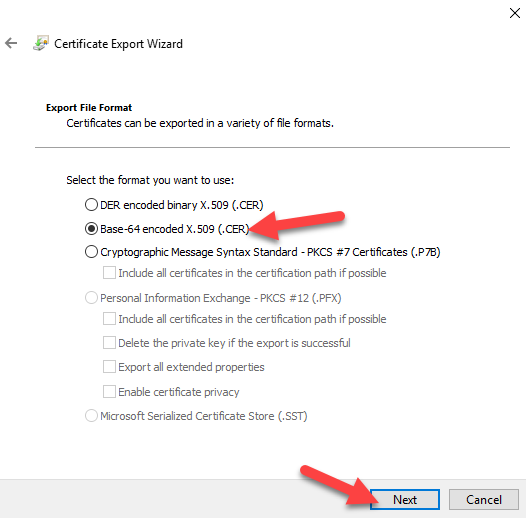
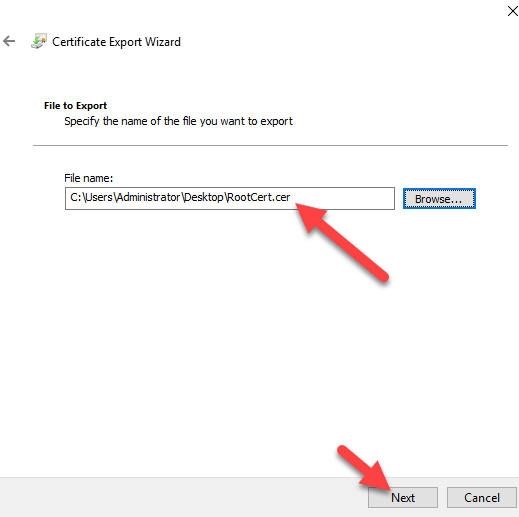
6. Go to our created Virtuel Network Gateway, and configure Point-to-Site configuration.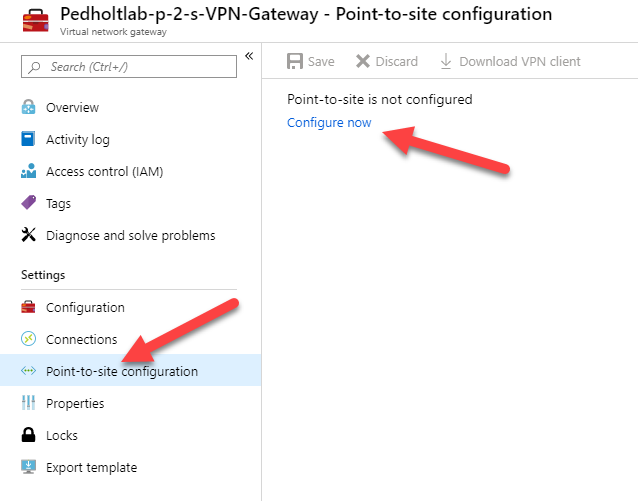
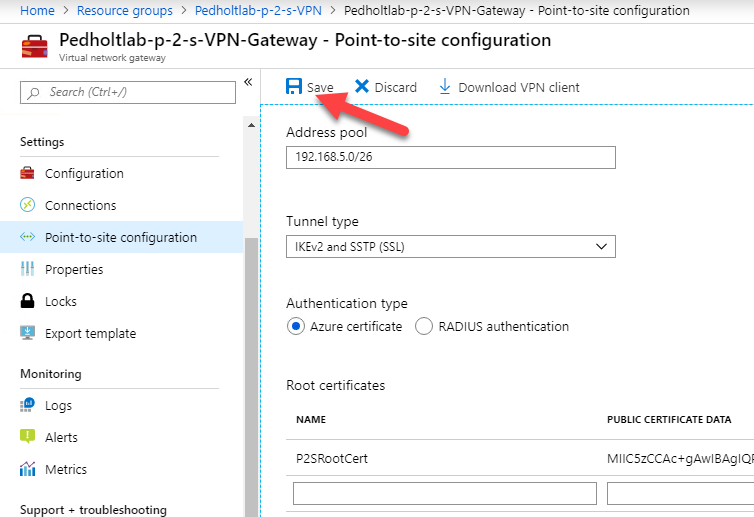
Fill out the configuration. Specify a address pool that the clients will have when connection to the VPN. Copy the certificate data we exported and paste it in Public Certificate Data. Then hit Save
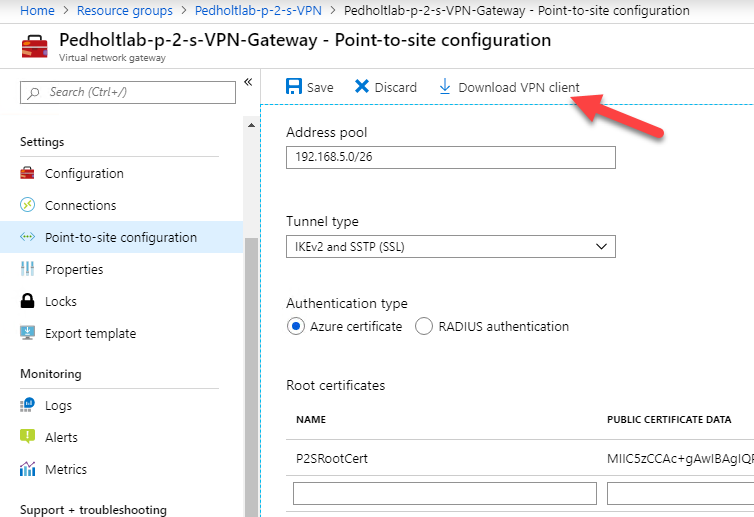
7. Lets test if it works!
Hit the download in the top, to download the Azure VPN Client.
Unzip the folder and run the installer
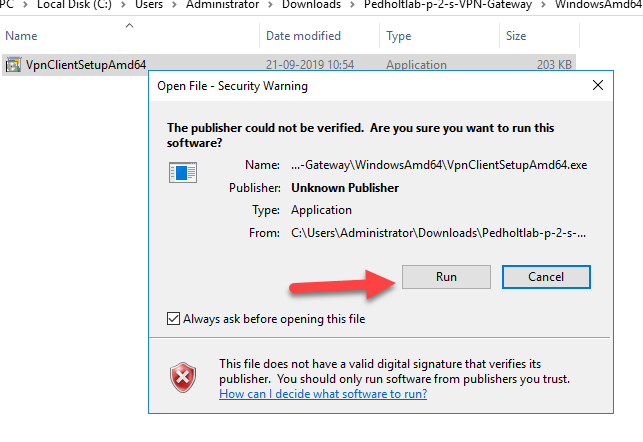
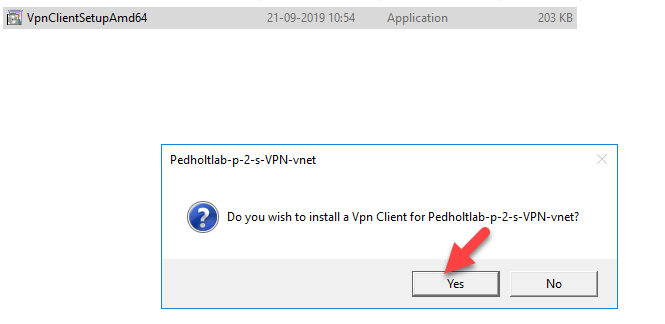
The VPN client are now installed, lets connect to it.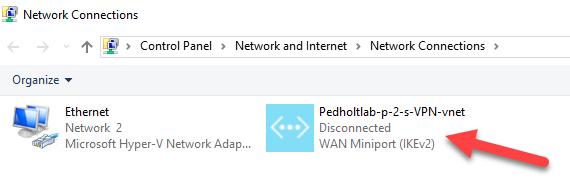
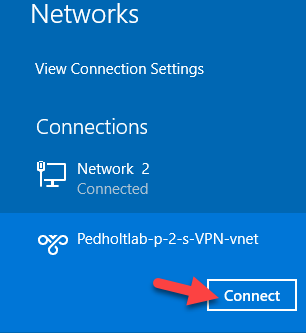
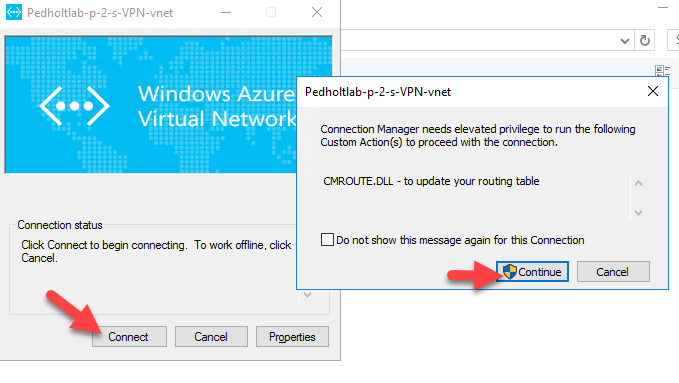
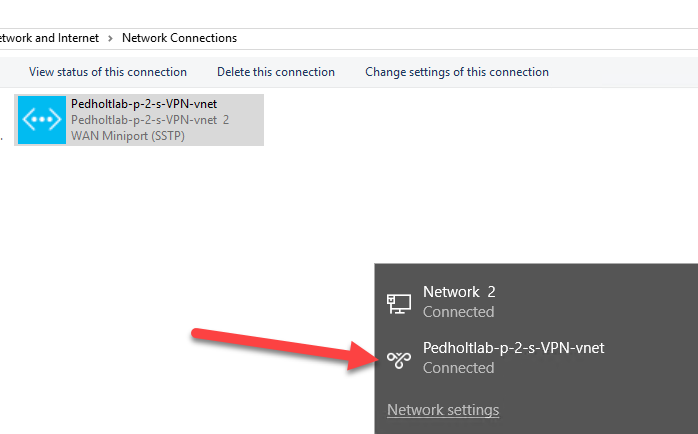
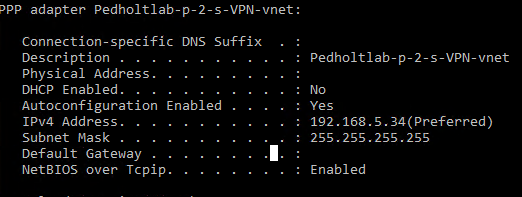
So far so good, now lets see if we can reach our server that we created in the start. Our server have got the IP address 192.168.4.4 from our Frontend Subnet.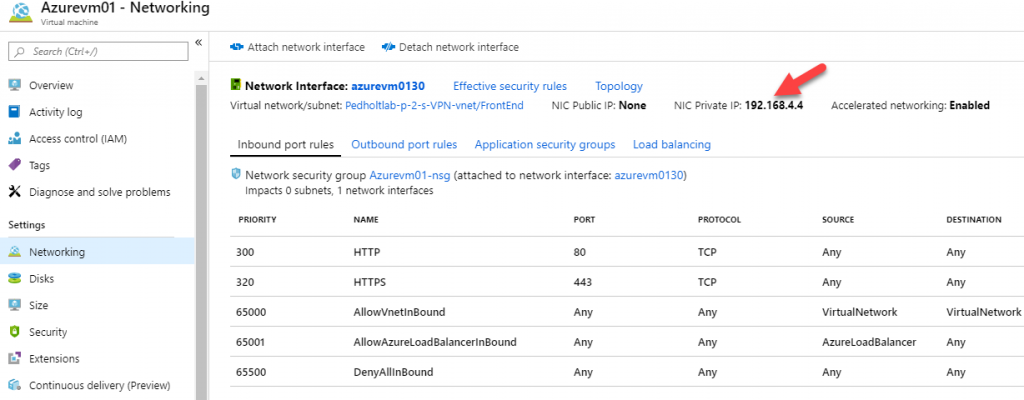
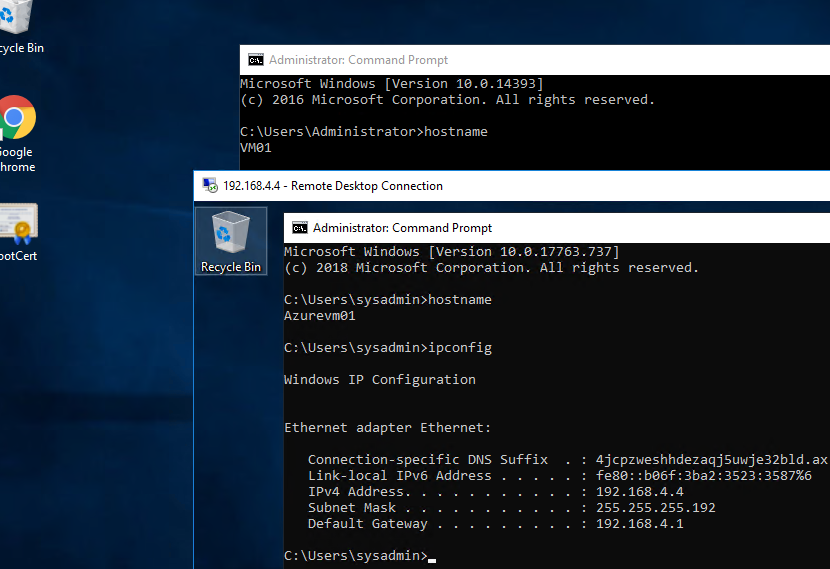
As you can see we can connect to the VM Azurevm01 that have the ip 192.168.4.4.
